Tiền pháp định
Các loại tiền điện tử
Không có kết quả cho ""
Chúng tôi không thể tìm thấy bất cứ thứ gì trùng khớp với tìm kiếm của bạn.Hãy thử lại bằng một cụm từ khác.
User reports serious security flaw in OKX crypto exchange’s two-factor authentication, user assets suffer hacker attack
Recently, we received a complaint from a user who said that his account assets on the OKX crypto trading platform were stolen by hackers. After our investigation and verification, we found that the OKX trading platform has two major security flaws:
- OKX crypto trading platform has a serious security flaw, its two-factor authentication mechanism can be bypassed by hackers, resulting in illegal login and operation of user accounts.
- OKX crypto trading platform’s P2P trading process has a design defect, its verification method can be selected and used by hackers, resulting in illegal sale and transfer of user assets.
The specific event process is as follows:
- The user was induced to download a browser trojan plugin when visiting a crypto information website. The plugin stole the user’s Google browser auto-fill account password information, including the OKX account password and the bound email password.
- Hackers used the stolen information to fake the user’s device information and browser information, and successfully logged into the user’s OKX account. The user did not receive any text message reminders, but found an email from OKX in his mailbox. The email showed that the login device was a US IP address and Firefox browser, which did not match the device and browser actually used by the user.
- Hackers tried to extract all the USDT in the user’s account, but because the user set up two-factor authentication for withdrawal, he needed to enter both text message verification code and email verification code, and the hacker failed to complete the withdrawal operation.
- Hackers changed to P2P trading mode and sold the USDT in the user’s account. Because P2P trading only requires choosing one of text message or email verification, hackers can use the stolen email password for verification. Hackers also bribed merchants to sell USDT at a low price.
- The user immediately transferred the remaining assets and applied to freeze the OKX account after finding the abnormal email.
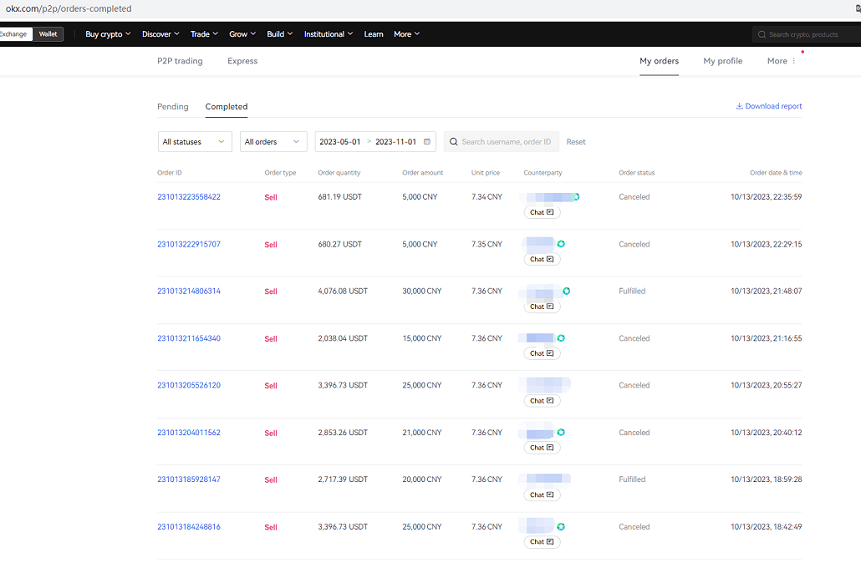
Hackers sell stolen funds through P2P (2 successful, 6 failed)
The user asked OKX the following questions about the theft:
- Why does the user’s account have two-factor authentication enabled, bind mobile phone text message verification, whether it is login or withdrawal, you need to enter a text message verification code, but hackers can log in to the account without text message verification?
- Why does withdrawal require entering text message verification code and email verification code to complete, but hackers fail to withdraw all USDT, but can sell USDT assets through P2P trading mode, bypassing withdrawal text message verification?
The user communicated with OKX customer service multiple times, but OKX customer service gave the following irresponsible and unprofessional replies:
- OKX has no security flaws and everything is running normally.
- The device logged in by hackers is a trusted device and does not require text message verification. But in fact, the last login of this device was more than a year ago, and it used a different browser.
- OKX’s login can switch verification methods, such as switching to email to receive text message login verification code on the web page, but in fact users cannot switch after operation, customer service said that App login can switch. But in fact App login requires face recognition verification, hackers cannot complete it through this method.
- OKX’s P2P trading users can choose text message or email verification by themselves, so hackers can sell USDT through P2P. But in fact this is a serious product security flaw, but it has not been taken seriously and improved by OKX.
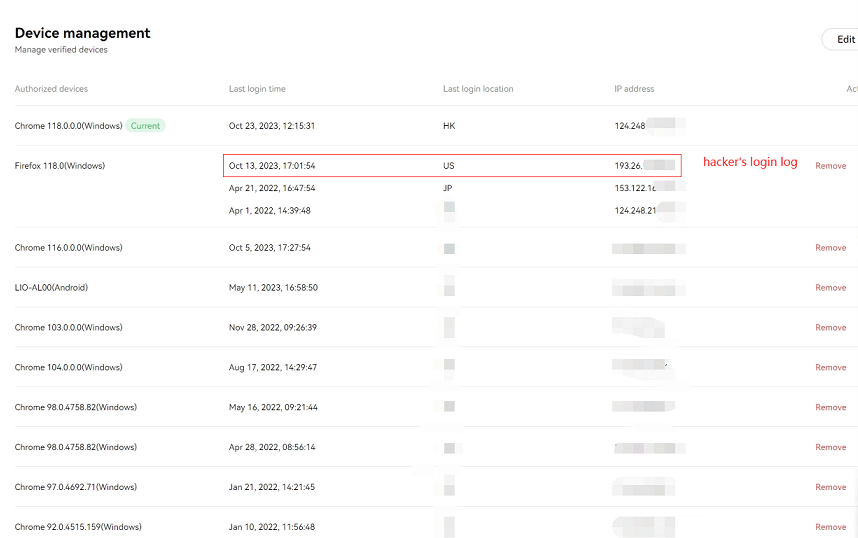
Hackers log in to OKX via FireFox
In response to this incident, as a third-party platform, we strongly express our dissatisfaction and condemnation of OKX crypto trading platform’s security flaws and customer service attitude. We believe that OKX crypto trading platform seriously damages users’ legitimate rights and interests, infringes on users’ privacy and property security, and violates the basic principles and ethics of the crypto industry. We urge OKX crypto trading platform to pay attention to this security incident and conduct a comprehensive inspection and optimization of its platform to eliminate all security risks and flaws. At the same time, we also remind users to pay attention to protecting their personal information and account security, do not trust any unknown links or plugins, do not disclose their passwords or verification codes to anyone.
Tìm chúng tôi trên:
X (Twitter) | Telegram | Reddit
Tải xuống ứng dụng CoinCarp ngay bây giờ: https://www.coincarp.com/app/